Saturday
Friday
Windows Registry
Editing the windows registry is one of the most powerful ways of manipulating you system settings, which is something that makes it equally dangerous.It is minefield filled with often cryptic configuration parameters which usually affect your system in ways you won’t even notice. it can completely mess up your system in such a way that you are unable to even boot into windows .Modify the right hardware settings, and your hardware gets boost, modify the wrong one, and you end up with a non- booting system.
Before you set up to d anything with the registry.
- If you are using the system restore /system protection feature in windows create a recovery point.
 |
| Windows Registry |
The windows Registry in any recent OS will display the following 5 root key entries.
N.
Wednesday
Disable Windows Logos
CODE

http://support.microsoft.com/?kbid=181348
or in other articles, You can copy the following messages into your notepad and save as *.reg, and use it..
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Keyboard Layout]
"Scancode Map"=hex:00,00,00,00,00,00,00,00,03,00,00,00,00,00,5b,e0,00,00,5c,e0,\
00,00,00,00
Tweak Firefox
Spyware,Mal-Ware,Hijackers,Dialers
HTTP and The Web (Internet)
Sunday
Virus Found
l if your PC is infected. Here's what to do if you suspect the worst.
Heard this one before? You must run antivirus software and keep it up to date or else your PC will get infected, you'll lose all your data,
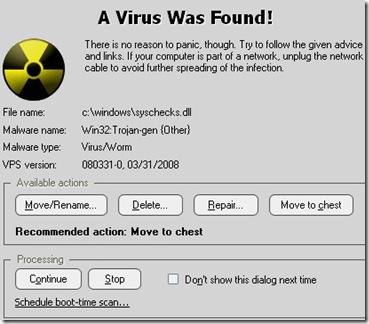
It happens. It's nothing to be ashamed of. But chances are, either you're infected right now, as we speak, or you will be very soon.
For a few days in late January, the Netsky.p worm was infecting about 2,500 PCs a day. Meanwhile the MySQL bot infected approximately 100 systems a minute (albeit not necessarily desktop PCs). As David Perry, global director of education for security software provider Trend Micro, puts it, "an unprotected [Windows] computer will become owned by a bot within 14 minutes."
Today's viruses, worms, and so-called bots--which turn your PC into a zombie that does the hacker's bidding (such as mass-mailing spam)--aren't going to announce their presence. Real viruses aren't like the ones in Hollywood movies that melt down whole networks in seconds and destroy alien spacecraft. They operate in the background, quietly altering data, stealing private operations, or using your PC for their own illegal ends. This makes them hard to spot if you're not well protected.
Is Your PC "Owned?"
I should start by saying that not every system oddity is due to a virus, worm, or bot. Is your system slowing down? Is your hard drive filling up rapidly? Are programs crashing without warning? These symptoms are more likely caused by Windows, or badly written legitimate programs, rather than malware. After all, people who write malware want to hide their program's presence. People who write commercial software put icons all over your desktop. Who's going to work harder to go unnoticed?
Other indicators that may, in fact, indicate that there's nothing that you need to worry about, include:
* An automated e-mail telling you that you're sending out infected mail. E-mail viruses and worms typically come from faked addresses.
* A frantic note from a friend saying they've been infected, and therefore so have you. This is likely a hoax. It's especially suspicious if the note tells you the virus can't be detected but you can get rid of it by deleting one simple file. Don't be fooled--and don't delete that file.
I'm not saying that you should ignore such warnings. Copy the subject line or a snippet from the body of the e-mail and plug it into your favorite search engine to see if other people have received the same note. A security site may have already pegged it as a hoax.
Sniffing Out an Infection
There are signs that indicate that your PC is actually infected. A lot of network activity coming from your system (when you're not actually using Internet) can be a good indicator that something is amiss. A good software firewall, such as ZoneAlarm, will ask your permission before letting anything leave your PC, and will give you enough information to help you judge if the outgoing data is legitimate. By the way, the firewall that comes with Windows, even the improved version in XP Service Pack 2, lacks this capability.
To put a network status light in your system tray, follow these steps: In Windows XP, choose Start, Control Panel, Network Connections, right-click the network connection you want to monitor, choose Properties, check "Show icon in notification area when connected," and click OK.
If you're interested in being a PC detective, you can sniff around further for malware. By hitting Ctrl-Alt-Delete in Windows, you'll bring up the Task Manager, which will show you the various processes your system is running. Most, if not all, are legit, but if you see a file name that looks suspicious, type it into a search engine and find out what it is.
Want another place to look? In Windows XP, click Start, Run, type "services.msc" in the box, and press Enter. You'll see detailed descriptions of the services Windows is running. Something look weird? Check with your search engine.
Finally, you can do more detective work by selecting Start, Run, and typing "msconfig" in the box. With this tool you not only see the services running, but also the programs that your system is launching at startup. Again, check for anything weird.
If any of these tools won't run--or if your security software won't run--that in itself is a good sign your computer is infected. Some viruses intentionally disable such programs as a way to protect themselves.
What to Do Next
Once you're fairly sure your system is infected, don't panic. There are steps you can take to assess the damage, depending on your current level of protection.
* If you don't have any antivirus software on your system (shame on you), or if the software has stopped working, stay online and go for a free scan at one of several Web sites. There's McAfee FreeScan, Symantec Security Check, and Trend Micro's HouseCall. If one doesn't find anything, try two. In fact, running a free online virus scan is a good way to double-check the work of your own local antivirus program. When you're done, buy or download a real antivirus program.
* If you have antivirus software, but it isn't active, get offline, unplug wires-- whatever it takes to stop your computer from communicating via the Internet. Then, promptly perform a scan with the installed software.
* If nothing seems to be working, do more research on the Web. There are several online virus libraries where you can find out about known viruses. These sites often provide instructions for removing viruses--if manual removal is possible--or a free removal tool if it isn't. Check out GriSOFT's Virus Encyclopedia, Eset's Virus Descriptions, McAffee's Virus Glossary, Symantec's Virus Encyclopedia, or Trend Micro's Virus Encyclopedia.
A Microgram of Prevention
Assuming your system is now clean, you need to make sure it stays that way. Preventing a breach of your computer's security is far more effective than cleaning up the mess afterwards. Start with a good security program, such Trend Micro's PC-Cillin, which you can buy for $50.
Don't want to shell out any money? You can cobble together security through free downloads, such as AVG Anti-Virus Free Edition, ZoneAlarm (a personal firewall), and Ad-Aware SE (an antispyware tool).
Just make sure you keep all security software up to date. The bad guys constantly try out new ways to fool security programs. Any security tool without regular, easy (if not automatic) updates isn't worth your money or your time.
Speaking of updating, the same goes for Windows. Use Windows Update (it's right there on your Start Menu) to make sure you're getting all of the high priority updates. If you run Windows XP, make sure to get the Service Pack 2 update. To find out if you already have it, right-click My Computer, and select Properties. Under the General tab, under System, it should say "Service Pack 2."
Here are a few more pointers for a virus-free life:
* Be careful with e-mail. Set your e-mail software security settings to high. Don't open messages with generic-sounding subjects that don't apply specifically to you from people you don't know. Don't open an attachment unless you're expecting it.
* If you have broadband Internet access, such as DSL or cable, get a router, even if you only have one PC. A router adds an extra layer of protection because your PC is not connecting directly with the Internet.
* Check your Internet ports. These doorways between your computer and the Internet can be open, in which case your PC is very vulnerable; closed, but still somewhat vulnerable; or stealthed (or hidden), which is safest. Visit Gibson Research's Web site and run the free ShieldsUP test to see your ports' status. If some ports show up as closed--or worse yet, open--check your router's documentation to find out how to hide them.
Auto End Tasks To Enable A Proper Shutdown
This reg file automatically ends tasks and timeouts that prevent programs from shutting down and clears the Paging File on Exit.
1. Copy the following (everything in the box) into notepad.
QUOTE
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management]
"ClearPageFileAtShutdown"=dword:00000001
[HKEY_USERS\.DEFAULT\Control Panel\Desktop]
"AutoEndTasks"="1"
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control]
"WaitToKillServiceTimeout"="1000"
2. Save the file as shutdown.reg
3. Double click the file to import into your registry.
NOTE: If your anti-virus software warns you of a "malicious" script, this is normal if you have "Script Safe" or similar technology enabled.
Thursday
Firefox
In the URL bar, type “about:config” and press enter. This will bring up the configuration “menu” where you can change the parameters of Firefox.
Note that these are what I’ve found to REALLY speed up my Firefox significantly - and these settings seem to be common among everybody else as well. But these settings are optimized for Broadband Connections.
Double Click on the following settings and put in the numbers below - for the true / false booleans - they’ll change when you double click.
Code:
browser.tabs.showSingleWindowModePrefs – true
network.http.max-connections – 48
network.http.max-connections-per-server – 16
network.http.max-persistent-connections-per-proxy – 8
network.http.max-persistent-connections-per-server – 4
network.http.pipelining – true
network.http.pipelining.maxrequests – 100
network.http.proxy.pipelining – true
network.http.request.timeout – 300
One more thing… Right-click somewhere on that screen and
- add a NEW -> Integer.
- Name it “nglayout.initialpaint.delay” and set its value to “0”.
Now you should notice you’re loading pages MUCH faster now!
Increase Speed of Computer
More Tweaking of Firefox :
The Forumz
The Hick
TeakFactor Very nice
Try it on your Own Risk The post Owner not Responsible.
What is Bandwidth ?

The amount of bandwidth a hosting company can provide is determined by their network connections, both internal to their data center and external to the public internet.
HTTP and The Web (Internet)
Good Safety Advice For Your Computer
Wednesday
Repair IE(Internet Explorer)
THE REPAIR PROCESS
Start the Registry Editor by typing regedit from the Run box.
Go to HKEY_LOCAL_MACHINE \ SOFTWARE \ Microsoft \ Active Setup \ Installed Components \ {89820200-ECBD-11cf-8B85-00AA005B4383}
and then right-click the “Is Installed value.” Click Modify. From there, you will change the value from 1 to 0. All right, go ahead and close the editor and reinstall IE from this location. /http://www.microsoft.com/windows/ie/default.mspx
IF SOMETHING GOES WRONG
If messing with the registry and something goes horribly wrong, you can use “Last Known Good Configuration (F8 Safe Mode)” or a Restore Point to get back to where you were before, with your settings. Then you can try again, this time taking care to watch the portion of the registry you are changing. Most people who have troubles with this end up changing the wrong registry key.
Hope this tut helps.
Try it on your own risk.
Install windows without Pressing Any key
An unattended Windows XP/2003 install can install all your software and settings along with Windows, and without you having to press a key,completely automated. Learn how over here:
CODE
Make your unattended setup now!
The above post only for knowledge.(try it on your own risk)
Sunday
Ethical Hacking
Ethical Hackers,with their knowledge,help to define the parameters of defense.They do “controlled” attacks,previously authorized by the organization, to verify the system’s defenses.they create groups to learn new attack techniques,exploitations and vulnerabilities, among others,They work as researchers for the security field.

Attack is the secret of defense;defense is the planning of attack by Sun Tzu
Ethical hacking is divided in several Phases :
- Attack Planning
- Internet Access
- Test and Execution of an attack
- Gathering information
- Analysis
- Assessment and Diagnosis
- Final Report.
TCP/IP model
Topologies
HTTP and The Web (Internet)
Saturday
Concepts of Networks
become familiar with the icons that represent the most common devices that are seen in the
basic schemes. These are:
 |
| Basic Network Device |
Topologies
TCP/IP model
Transport
More....
TCP/IP model
(Defense Advanced Research Project Agency) in the 1970s. TCP/IP was designed to be an
open standard that anyone could use to connect computers together and exchange
information between them. Ultimately, it became the basis for the Internet
The TCP/IP model defines four totally independent layers into which it divides the process of
communication between two devices. The layers through which it passes information
between two devices are
Application :
The application layer is the layer nearest the end user. This is the layer that is in charge of
translating data from applications into information that can be sent through the network.
The basic functions of this layer are:
- Representation.
- Codification.
- Dialog Control.
- Application Management.
Transport :
The transport layer establishes, maintains and finishes virtual circuits for information transfer. It
provides control mechanisms for data flow and allows broadcasting, and it provides
mechanisms for the detection and correction of errors. The information that arrives at this
layer from the application layer is divided into different segments. Information that comes to
the transport layer from the internet layer is delivered back to the application layer through
ports.
The basic functions of this layer are:
- Reliability.
- Flow Control.
- Error Correction.
- Broadcasting.
Internet:
This layer divides the segments of the transport layer into packets and sends the packets
across the networks that make up the Internet. It uses IP, or internet protocol addresses to
determine the location of the recipient device. It does not ensure reliability in the
connections, because this is already taken care of by the transport layer, but it is responsible
for selecting the best route between the originating device and the recipient device.
Network Access :
This layer is in charge of sending information at both the LAN level and the physical level. It
transforms all the information that arrives from the superior layers into basic information (bits)
and directs it to the proper location. At this level, the destination of the information is
determined by the MAC, or media access control, address of the recipient device.
Topologies
share resources, such as hard drives, printers and Internet connections, and an administrator
can control how these resources are shared. When a LAN is being designed, it is possible to
choose any of the following physical topologies:
In a bus topology, all the computers are connected to a single means of transmission, and
each computer can communicate directly with any of the others.
In the ring configuration,each computer is connected to the following one, and the last one to the first, and each computer can only communicate directly with the two adjacent computers.
In the star topology, none of the computers are directly connected with others. Instead they are
connected through a central point and the device at that central point is responsible for
relaying information from computer to computer. If several central points are connected to each other, an extended star topology is obtained.
In a star or extended star topology, all the central points are peers, that is, each exchanges information on an equal basis. However, if you connect two star or extended star networks together using a central point which controls or limits the exchange of information between the two networks, then you have created a
single, hierarchical network topology.



